The web development ecosystem experienced rapid growth following the pandemic, as companies invested heavily in technological advancements. Node.js is the fundamental technology standard for modern industry operations because it supports numerous web applications across large technology corporations and small startup businesses. Node.js provides attackers with excellent power when security measures are not adequately implemented.
Key Takeaways
- Node.js applications require auditing dependencies, validating inputs, and rate limiting to reduce their attack surfaces.
- Strong authentication and authorization strategies, including secure password hashing and proper JWT configurations, are essential for protecting user data.
- Environment variables should be used for sensitive configuration and secret management, and HTTPS should be used for secure data transmission.
- Implementing structured error handling and complete logging systems protects application integrity by hiding system internals.
- Security requires ongoing lifecycle management, including continuous monitoring and configuration validation, and support for responsible vulnerability disclosure through security.txt mechanisms.
Why Security Matters More Than Ever
Before diving into technical details, let's understand why securing Node.js applications has become critical:
- Data Protection: Your application likely handles sensitive information such as user credentials, payment details, and personal data—today's digital gold. Users have placed their trust in you to protect this information.
- Compliance Requirements: Regulations such as GDPR and CCPA in various countries impose substantial fines for data breaches. Numerous case studies document these consequences.
- Business Continuity: A data breach can result in substantial business and operational losses. Depending on the size of your application, it can be disastrous for your business and erode customer trust in your company.
- Growing Attack Surface: The risk of malicious package installation attacks is a genuine concern. You might accidentally install packages that contain malware, allowing malicious actors to gain access to your application.
1. Keep Your Dependencies Fresh and Secure
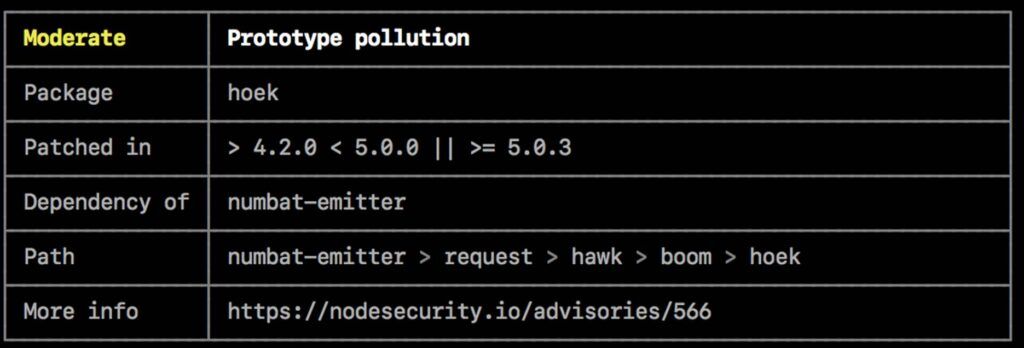
In the npm ecosystem, anyone can publish packages to the npmjs website. One wrong spelling can lead you to download a legitimate-looking library that isn't genuine. Even when using the correct libraries, their dependencies can infect your system.
Regular Dependency Auditing
Start by regularly auditing your dependencies:
``` # Check for known vulnerabilities npm audit # Automatically fix issues where possible npm audit fix # For more detailed analysis npm audit --audit-level moderate ```Using Advanced Security Tools
For enterprise applications, consider using comprehensive tools:
``` # Install Snyk globally npm install -g snyk # Test your project snyk test # Monitor continuously snyk monitor ```Dependency Update Strategy
Create a systematic approach to updates:
{
"scripts": {
"security-check": "npm audit && snyk test",
"update-check": "npm outdated",
"safe-update": "npm update --save"
}
}
2. Implement Robust Authentication and Authorization
Authentication is your first line of defense—it gives users access to your database. Weak authentication mechanisms are like leaving your front door unlocked.
Password Security Best Practices
Never store passwords in plain text. Use strong hashing algorithms:
const bcrypt = require('bcrypt');
// Hash password during registration
async function hashPassword(plainPassword) {
const saltRounds = 12; // Higher is more secure but slower
return await bcrypt.hash(plainPassword, saltRounds);
}
// Verify password during login
async function verifyPassword(plainPassword, hashedPassword) {
return await bcrypt.compare(plainPassword, hashedPassword);
}Implementing JWT Securely
JSON Web Tokens are popular for credential management, but they require proper implementation and configuration. They are strings hashed based on your secret but can be dangerous because anyone can read what's stored in them. Proper implementation is essential:
const jwt = require('jsonwebtoken');
const crypto = require('crypto');
// Generate a secure secret (do this once and store securely)
const JWT_SECRET = process.env.JWT_SECRET || crypto.randomBytes(64).toString('hex');
// Create token with expiration
function createToken(userId) {
return jwt.sign(
{ userId, timestamp: Date.now() },
JWT_SECRET,
{
expiresIn: '1h',
issuer: 'your-app-name',
audience: 'your-app-users'
}
);
}
3. Input Validation and Sanitization
"Never trust user input" is a famous quote among developers. You should always validate and sanitize all data from external sources, especially user input.
Using Zod for Schema Validation
Zod provides a modern, TypeScript-first approach to validation with better type safety. Zod is a TypeScript-first validation library. Using Zod, you can define schemas to validate data, from a simple string to a complex nested object.
4. Rate Limiting and DDoS Protection
Users can abuse specific endpoints, which may be costly to run. You can implement rate limiting to protect your application from abuse and prevent budget overruns.
const rateLimit = require('express-rate-limit');
const slowDown = require('express-slow-down');
// General rate limiting
const generalLimiter = rateLimit({
windowMs: 15 * 60 * 1000, // 15 minutes
max: 100, // Limit each IP to 100 requests per windowMs
message: {
error: 'Too many requests from this IP, please try again later'
},
standardHeaders: true,
legacyHeaders: false,
});Similarly, you can create other rate limiters for authentication and routes, such as image loading or running expensive algorithms.
5. Environment Configuration and Secrets Management
Your application may use different services or secrets that should remain confidential, such as database credentials. You don't want unauthorized access to your database.
When learning development, developers often hard-code secrets in their code. This is very dangerous for production because as your app grows, your code might be leaked through any mishap. If your secrets are revealed, they can provide direct access to your systems.
Always keep sensitive information out of your codebase:
// Never do this
const dbPassword = 'mySecretPassword123';
const apiKey = 'sk-1234567890abcdef';
// Use environment variables
const dbPassword = process.env.DB_PASSWORD;
const apiKey = process.env.API_KEY;
// Validate required environment variables
function validateEnvironment() {
const required = ['DB_PASSWORD', 'JWT_SECRET', 'API_KEY'];
const missing = required.filter(key => !process.env[key]);
if (missing.length > 0) {
console.error('Missing required environment variables:', missing);
process.exit(1);
}
} validateEnvironment();6. Code Quality and Best Practices: Bad vs Good Code
Writing secure code isn't just about implementing security features—it's also about writing clean, maintainable code that reduces the likelihood of introducing vulnerabilities. Poor coding practices often create security holes that attackers can exploit, while good practices inherently strengthen your application's security posture.
Why Code Quality Matters for Security
When developers write sloppy or unmaintainable code, they inadvertently create vulnerabilities. Rushed implementations, poor error handling, and unclear logic paths contribute to security weaknesses. The relationship between code quality and security is stronger than most developers realize.
Modern JavaScript applications require disciplined approaches to asynchronous operations, error handling, and resource management. Each of these areas presents opportunities for both security improvements and security disasters.
Async/Await vs Promises: More Than Just Syntax
The choice between async/await and traditional promise chains isn't just about readability—it's about security and reliability. Promise chains create complex nested scopes where variables become undefined, leading to runtime errors that expose sensitive information or create unexpected application states.
The Problem with Promise Chains: Promise chains often suffer from scope issues where variables declared in one .then() block aren't available in subsequent blocks. This leads to reference errors, undefined behavior, and potential security holes where error states aren't correctly handled.
// Scope issues and poor error handling
function getUserData(userId) {
return db.users.findById(userId)
.then(user => {
return db.profiles.findByUserId(user.id);
})
.then(profile => {
return { user: user, profile }; // ReferenceError: user is not defined
})
.catch(error => {
console.log(error); // Poor error handling
});
}Async/Await Advantages: Async/await provides a more precise variable scope, better error handling, and more predictable execution flow. This reduces the chance of exploiting undefined states.
async function getUserData(userId) {
try {
const user = await db.users.findById(userId);
const profile = await db.profiles.findByUserId(user.id);
return { user, profile };
} catch (error) {
logger.error('User data retrieval failed', { userId, error: error.message });
throw new Error('Unable to retrieve user information');
}
}Database Security Through Better Patterns
Database interactions are among the most critical areas where code quality has a direct impact on security. String concatenation in queries is a classic example of how poor coding practices create severe vulnerabilities.
The SQL Injection Problem: When developers concatenate user input directly into SQL queries, they create opportunities for SQL injection attacks to occur. This isn't just a theoretical concern—it's one of the most common attack vectors for web applications.
Beyond SQL Injection: Even when using ORMs, poor patterns like callback hell make it challenging to implement proper transaction management, leading to data inconsistency and potential race conditions that attackers can exploit.
// Secure parameterized query
const query = 'SELECT * FROM users WHERE email = $1';
const result = await db.query(query, [email]);Error Handling: The Security Boundary
Error handling is where many applications leak sensitive information. Poor error handling doesn't just create bad user experiences—it provides attackers with valuable reconnaissance information about your system's internals.
Information Leakage Through Errors: When applications expose stack traces, database error messages, or internal system details through error responses, they provide attackers with valuable insights into the system architecture, file structures, and potential vulnerabilities.
Silent Failures: On the other hand, silently ignoring errors can mask security incidents, making it impossible to detect ongoing attacks or system compromises.
Proper Error Boundaries: Good error handling creates clear boundaries between internal system information and external error responses. It logs detailed information for developers while providing safe, generic messages to users.
Configuration Management as a Security Layer
How you manage configuration and environment variables directly impacts the security of your application. Hardcoded secrets, missing validation, and poor configuration patterns create vulnerabilities that persist throughout the application's lifecycle.
The Hardcoded Secret Problem: Hardcoded credentials and API keys in source code represent one of the most dangerous security antipatterns. These secrets often end up in version control systems, get shared across teams, and become impossible to rotate without code changes.
Environment Variable Validation: Simply using environment variables isn't enough; you need to validate that the required variables exist and contain appropriate values. Missing validation can cause applications to start in insecure states or fail unpredictably.
Architectural Patterns and Security
How you structure your application code affects the ease of implementing and maintaining security measures. Monolithic route handlers that mix validation, business logic, and data access make it difficult to apply security controls consistently.
Separation of Concerns: When validation logic is mixed with business logic and data access, it becomes easy to bypass security checks accidentally. Clear separation makes security controls more visible and maintainable.
Middleware Patterns: Well-structured middleware pipelines ensure that security checks are consistently applied across your application. They also make it easier to audit and test security controls.
Resource Management and Denial of Service
Poor resource management can lead to performance issues and create opportunities for denial-of-service attacks. Memory leaks, unclosed connections, and unbounded caches represent potential attack vectors.
Memory-Based Attacks: Attackers can exploit applications with poor memory management by triggering memory leaks or causing excessive memory allocation, which can lead to application crashes or server instability.
Connection Pool Exhaustion: Attackers who trigger resource exhaustion can overwhelm applications that don't properly manage database connections or external API calls.
The Compound Effect of Good Practices
Each good practice might seem minor, but they compound to create significantly more secure applications. When you combine proper async/await usage, parameterized queries, comprehensive error handling, secure configuration management, and good architectural patterns, you create multiple layers of defense against various attack vectors.
The key insight is that security isn't just about adding security features—it's about building applications where insecure states are challenging to reach and security violations are immediately visible.
7. Error Handling and Logging
Even though your app runs perfectly for you, it might break when users start using it, potentially revealing critical information to users who shouldn't have access to it. This becomes a nightmare if someone gains access to sensitive data about your app. You should consistently implement logging and error handling to provide a better user experience and gain insights into your application.
You can use Winston to log events and errors:
const winston = require('winston');
// Configure logging
const logger = winston.createLogger({
level: 'info',
format: winston.format.combine(
winston.format.timestamp(),
winston.format.errors({ stack: true }),
winston.format.json()
),
transports: [
new winston.transports.File({ filename: 'error.log', level: 'error' }),
new winston.transports.File({ filename: 'combined.log' })
]
});
// Global error handler
app.use((err, req, res, next) => {
// Log the error
logger.error('Unhandled error', {
error: err.message,
stack: err.stack,
url: req.url,
method: req.method,
ip: req.ip
});
// Don't leak error details in production
if (process.env.NODE_ENV === 'production') {
res.status(500).json({
error: 'Something went wrong. Please try again later.'
});
} else {
res.status(500).json({
error: err.message,
stack: err.stack
});
}
});
// Graceful error handling for async routes
const asyncHandler = (fn) => (req, res, next) => {
Promise.resolve(fn(req, res, next)).catch(next);
};
// Usage
app.get('/api/users', asyncHandler(async (req, res) => {
const users = await User.findAll();
res.json(users);
}));Keep Your Responses To the Point
Consider implementing response filtering at the controller level to enhance security. Create a standardized response for matters that explicitly whitelist which fields should be returned for each endpoint. This approach forces you to be intentional about what data leaves your server rather than accidentally oversharing.
8. Creating a Clear Path for Security Reports
Last but not least, vulnerabilities will slip through no matter how carefully you code. It's not a matter of if, but when. When someone discovers a security issue in your application, will they be able to reach you easily, or will they give up and potentially sell that information to less friendly parties?
Security researchers and ethical hackers are doing you a massive favor when they find and report vulnerabilities. These are the good guys – they could easily exploit or sell what they see on dark markets, but instead, they're choosing to help you fix the problem. At the very least, make it easy for them to contact you.
This is where security.txt comes in. It is a "How to Help Me" guide for security researchers. It's a simple, standardized format that tells people exactly how to report security issues to you, and it resides at the root of your domain, where anyone can find it.
The beauty of security.txt lies in its simplicity. Here's what a real-world example might look like:
Contact: security@yourcompany.com
Contact: https://yourcompany.com/security-report
Encryption: https://yourcompany.com/pgp-key.asc
Preferred-Languages: en, es
Policy: https://yourcompany.com/security-policy
Expires: 2025-12-31T23:59:59.000ZLet's break this down piece by piece. The Contact field is your lifeline – this is how researchers will reach you. Please note that you can have multiple contact methods. Perhaps you would like to offer both an email and a web form, providing people with options tailored to their preferences and the sensitivity of their reporting.
Beyond the basic security.txt file, consider creating a dedicated security page on your website. This provides you with more space to explain your process, including how quickly researchers can expect a response, what information is required in a comprehensive vulnerability report, and what your disclosure timeline looks like. Some companies even offer bug bounty programs or public recognition for researchers who help them improve their security.
The key is making the entire process as frictionless as possible. Security researchers are busy individuals, often volunteering their time to help make the internet a safer place. If reporting a vulnerability to you requires jumping through hoops, filling out complex forms, or navigating corporate bureaucracy, they might move on to the next target.
Remember, this isn't just about being nice – it's about protecting your business. A vulnerability reported through proper channels gives you time to fix it before it's exploited. A vulnerability discovered by malicious actors gives you no warning at all. The choice is pretty straightforward.
Security Checklist for Production
Here's a pre-deployment security checklist to ensure you've covered all bases:
- All dependencies are up to date and audited
- Security headers are properly configured
- Input validation is implemented for all endpoints
- Authentication and authorization are properly implemented
- Rate limiting is configured
- Sensitive data is properly encrypted
- Environment variables are used for secrets
- Error handling doesn't leak sensitive information
- HTTPS is enforced
- Logging and monitoring are configured
- Database queries use parameterized statements
- File upload restrictions are in place
- CORS is properly configured
Conclusion
A production-grade Node.js security system needs multiple protection layers, including auditing, validation, authentication, error handling, and secure configurations. These best practices help organizations minimize vulnerabilities while maintaining long-term application resilience.

