X-VPN today shared findings from an internal review of Blind In/On-Path analysis techniques. Our tests indicate these methods read side-channel traces from packet handling; they do not decrypt VPN content. The signal we measured maps to operating-system routing behavior—most noticeably on Android—rather than to flaws in X-VPN tunneling or cryptography.
How Blind In/On-Path analysis works
On an untrusted network (e.g., a hostile hotspot), an attacker can send crafted probes and watch how a device reacts. Minor timing or response differences can indicate that a VPN session exists or, in some conditions, disrupt a connection. None of this reveals plaintext moving inside the encrypted tunnel.
What we observed across platforms
Apple & Microsoft (iOS, macOS, Windows)
In our controlled runs, we did not observe a stable, reproducible signal comparable to Android. Encrypted sessions on these systems operated as expected.
Across platforms, X-VPN’s crypto stack—AES-GCM, TLS-based handshakes, and the Everest family—functioned as intended. Protocol diversity remains available (WireGuard, OpenVPN, and Everest-TCP) to maintain session resilience.
Linux
Similar signals can arise under permissive settings, but Linux allows administrator controls. X-VPN now filters unexpected traffic at the interface layer to shrink the response surface.
Android
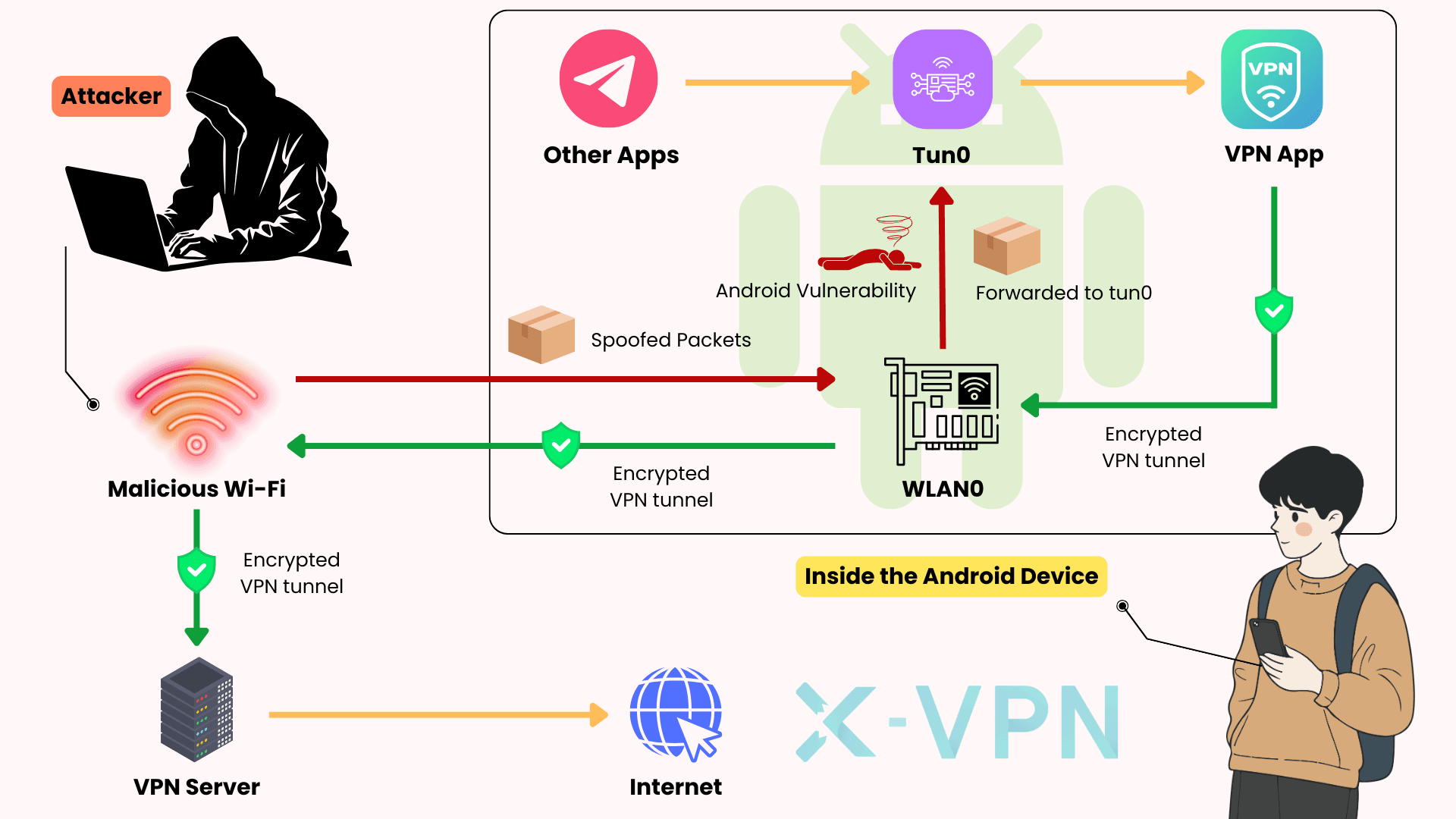
In internal testing, Strict reverse-path validation is not enforced by default (i.e., rp_filter is not applied strictly), which may allow forged packets to traverse between interfaces. Probes aimed at the virtual tunnel (e.g., tun0) produced measurable responses on open Wi-Fi. Because Android clients rely on the VpnService API and cannot change kernel parameters, a complete fix requires OS-level changes.
Across all platforms, X-VPN’s stack—AES-GCM, TLS-based handshakes, and the Everest family—functioned as intended. Protocol diversity (WireGuard, OpenVPN, and Everest-TCP) maintains session resilience.
Summary of findings
No data exposure detected
Encryption remained sound, and our no-logs position held throughout validation.
Internal review shows the clearest signal on Android
Permissive routing checks may allow spoofed probes to elicit observable device responses.
Linux now hardened
Interface-level controls drop unsolicited packets before they reach the tunnel.
Independent audit in progress
Scope includes logging enforcement, encryption behavior, and tunnel integrity.
“This is a boundary question—where OS networking ends and where a VPN’s remit begins,” said Luke Murphy, Technical Editor at X-VPN. “Our tunnels stayed encrypted and controls performed as designed. The residual signal aligns with platform routing defaults, not with broken cryptography.”
Actions taken
Coordinated disclosure to Google
X-VPN provided scope, observations, and replication artifacts to the Android security team for vendor-side assessment.
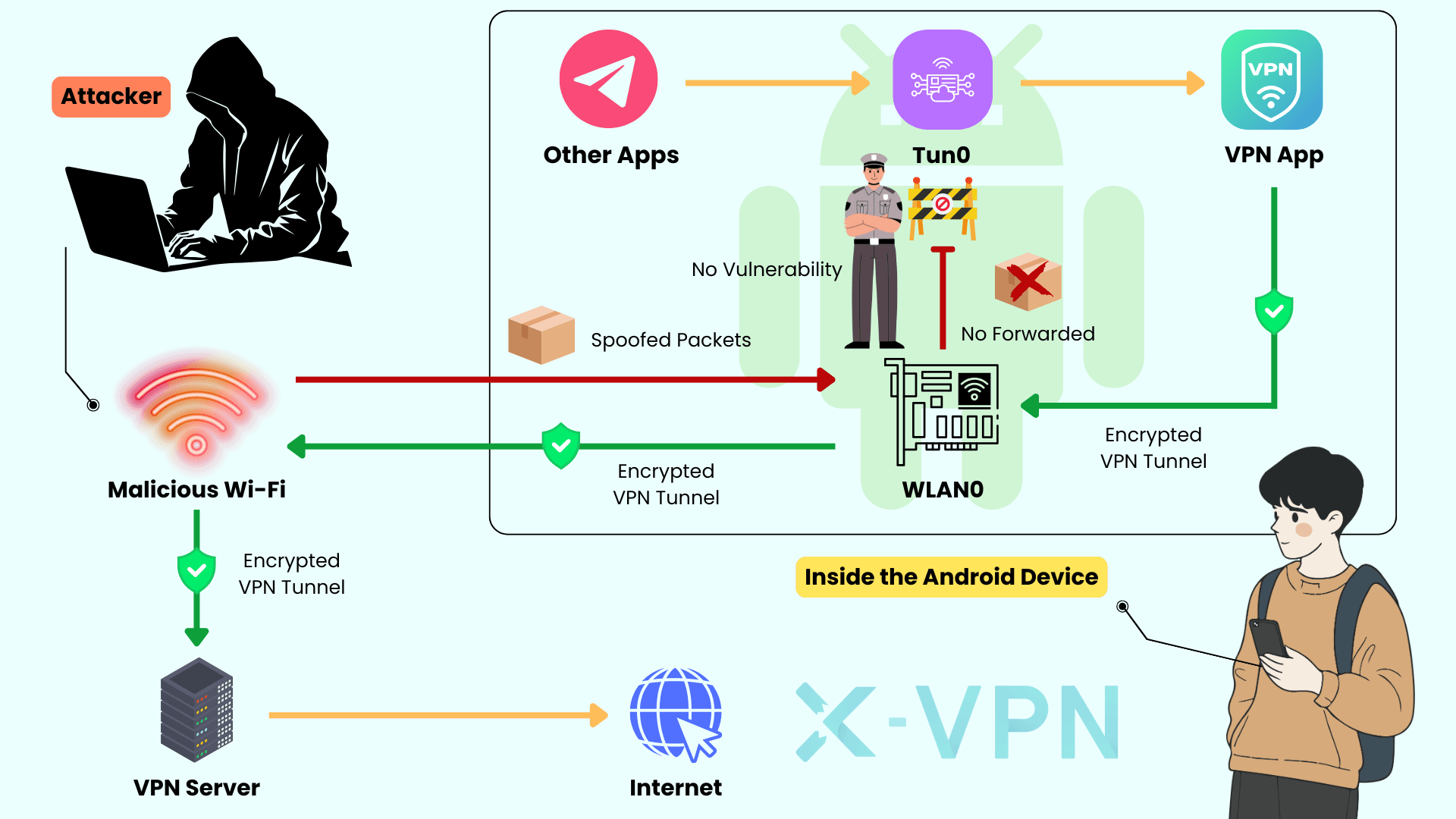
Linux hardening shipped
The client drops traffic directed at the tunnel unless it matches expected routes, reducing side-channel noise.
Android research continues
App-layer heuristics (e.g., detecting abnormal probe patterns) are being evaluated, with caution about performance trade-offs and the limits of client-only defenses.
Tighter monitoring
Thresholds for handshake anomalies and downgrade attempts have been raised across apps.
Practical guidance for Android users
Until upstream platform changes land, X-VPN recommends:
- Prefer mobile data or trusted Wi-Fi; avoid unknown public hotspots.
- Use HTTPS-first apps and sites.
- Enable Kill Switch in the Android app. If the tunnel drops, internet access is cut off, reducing exposure on hostile networks.
- Keep system firmware and the VPN app up to date.
X-VPN’s Android app offers Kill Switch to both Free and Premium users. Premium plans allow five simultaneous devices and include optimized streaming servers (e.g., for Netflix). The Free plan provides encrypted tunneling and selected locations without requiring an email address.
Looking ahead
VPNs protect traffic in transit, but platform defaults and real-world network conditions shape what attackers can observe from the outside. By documenting the boundary between OS routing and VPN control—and by hardening Linux, coordinating with Android security, and tightening detection—X-VPN aims to provide practical, verifiable protection steps without overstating scope.